The traditional idea of the well-defined network perimeter is outdated in a world where organizations are increasingly moving applications and data to cloud services, embracing a highly mobile remote workforce, and dealing with a significantly growing number of devices attaching to the corporate network. Many digital transformation initiatives are forcing businesses to rethink their enterprise security architecture. As organizations go through these changes, security concerns are paramount with cyber attacks on the rise.
“In March, there was a 30,000% increase in COVID-19 related attacks and malware.”(Source: Zscaler)
Today’s new reality in an increasingly perimeter-less world begs the question: how does an organization protect itself? The Zero Trust framework presumes bad actors are already in the network. The approach deploys multiple strategies such as (a) identity and access management, (b) multifactor authentication, (c) encryption, (d) risk scoring, and (e)role-based access controls to enforce strict governance policies. These policies provide user access to specific applications and resources aligned with their roles and responsibilities. This limits not only north-south movement in the network, but also east-west lateral movement across the network.
Four (4) Things You Need To Know
The methodologies that enable Zero Trust accomplish five (5) core tasks:
Micro-segmentation. Micro-segmentation is a method of creating secure zones in data centers, cloud deployments, and even applications, allowing organizations to isolate workloads from one another and secure them individually. It is aimed at making network security more granular. Using micro-segmentation, files in a network can be placed in separate secure zones. A user or program with access to one of those zones will not be able to access any of the other zones without separate authorization, tying security to individual workloads.
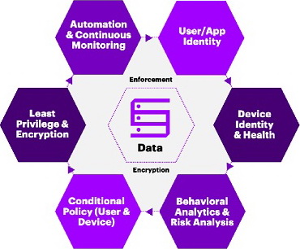
- Least Privilege Access. Zero-Trust is based on granting least privilege access. However, the access is only granted on verification of multiple contextual environmental variables at each request, such as: (a) who is requesting access, (b) what is the context of the request, and (c) what is the risk of access to the environment. Zero-trust no longer provides trust to anyone or anything connecting to valued systems. It treats equally traffic originating from within the network as well traffic arriving externally – users, devices, even API’s are all treated the same. This enables minimization of the attack surface, it improves audit, and reduces the risk and costs of security breaches.
- Multi-factor Authentication (MFA). MFA is a core value of zero trust security. It means simply requiring more than one piece of evidence to authenticate a user, entering a password alone is not enough to gain access. The use of two-factor authorization—the addition of a code sent to another device — is now widely used and accepted by consumers and stakeholders. Other forms of authentication — biometrics — are emerging to bolster identity verification.
Application Behavior and Visibility. A benefit of micro-segmentation is the enablement of application security that builds in policies defining allowed behavior and protection for each individual build. As example, ideation through development occurs in an environment isolated from the rest of the network so that any breach of an application will be contained and prevented from spreading into the rest of the network. Visibility into application behavior on devices that access applications also needs to be taken into account so anomalous activity can be detected and action can be taken more quickly.
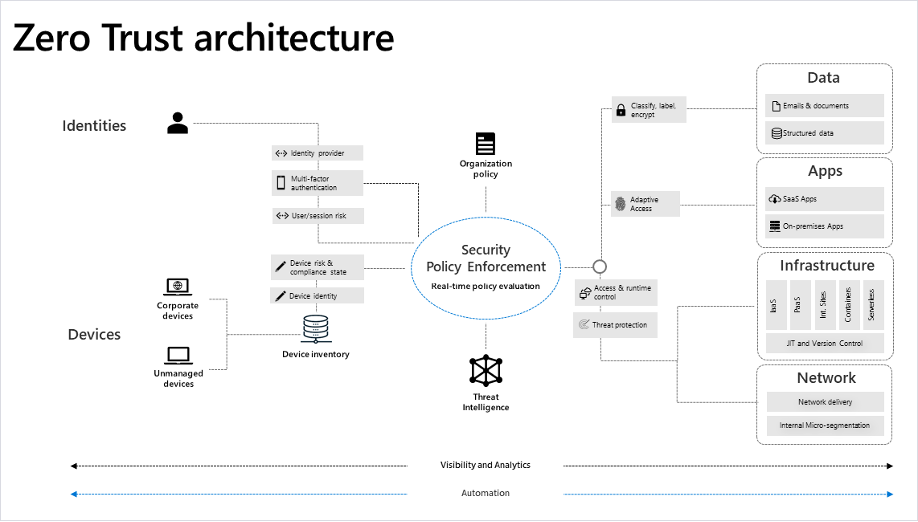
Designing and Building
Use a five (5) step model for implementing and maintaining a Zero Trust network:
- Define the protect surface. In the Zero Trust defining the scope of the protect surface in manageable portions is critically important. The protect surface should include the critical
- Map the transactions flows. How traffic moves across a network should define how it is protected. Therefore it is essential to gain contextual insight on the interdependencies of your data, application, assets and services – the DAAS. Documenting the interaction between specific resources allows the ability to properly enforce controls. It also provides valuable context to ensure the controls help protect the data.
- Architect a Zero Trust network. Zero Trust networks are built from the ground up, architected and customized around specific requirements for the protect surfaces. However it is imperative that the protect surface and transaction flow maps be completed first.
- Create the Zero Trust policy. Once the Zero Trust network has been architected, the next step is to define and whitelist which resources should have access to the others. The questions of “who, what, when, where, why and how” work well here.
- Monitor and maintain the network. Lastly, the final step is to ensure logging is enabled, all logs are reviewed (both internal and external) and data is analyzed in a timely manner. Visibility should be all way through Layer 7 of the OSI model.
Upon completing the first protect surface for your organization, this model can be iteratively and easily expanded to other data sets, applications, assets and services from legacy or modern systems. It can be implemented in a cost-effective and non-destructive way.
Zero Trust and the Future of Work
Security objectives and best practices to keep mind while designing and building a Zero Trust environment that serves today’s needs and into the future should include these considerations:
- Think Anytime, Anywhere. Secure applications, data, users, devices and network traffic through persistent protection, all with the same degree of effectiveness regardless of location. The user experience should be frictionless and easy to deploy.
- Build for Resilience. As organizations mature their continuity of operations and crisis management plans, a Zero Trust architecture allows organizations to adapt and move quickly to changing environments and realities, in addition to providing strong cybersecurity best practices.
Zero Trust means different things to different organizations. It is an approach, a framework. Zero Trust is not a specific tool or set of tools. It can be adapted to many use cases, particularly for remote work, teleworking, and BYOD (Bring Your Own Device) typically a practice still not considered secure, and it can be implement one defined protect surface at a time.
As senior leaders we are asked to be more strategic and drive revenue through technologies and integration as the business goals and needs expand. At the same time, cybersecurity is an incredibly complex problem to solve from both the end user side and in the data center as attack surfaces become even broader. It’s no longer a question of “if” a breach will happen but “when.” Zero Trust provides a scalable adaptive solution.
Author:
Laszlo S. Gonc, CISSP, First Senior Fellow, DivIHN Cybersecurity Center of Excellence












